Last week, Thursday, May 18, 2023, in addition to iOS 16.5, iPadOS 16.5, and macOS Ventura 13.4, Apple also released the following updates: macOS Big Sur 11.7.7, macOS Monterey 12.6.6, iOS 15.7.6, iPadOS 15.7.6. 16.5, tvOS 9.5, watchOS 16.5 and Safari XNUMX. The fact that so many systems, including older systems, have missed an update shows quite clearly that security gaps must have been closed. Apple has now confirmed this in a corresponding overview of the update content. This shows that dozens of security gaps have been closed with the individual updates. So you should install the respective update on iPhone, Mac, Apple Watch and Co. as soon as possible.

Chapter in this post:
This is how you can find the system update on your device
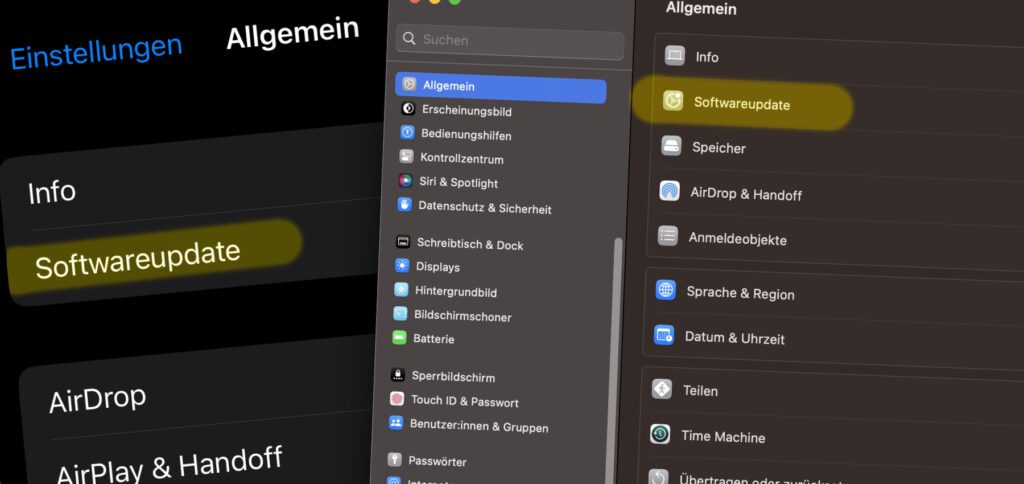
In the settings or system settings of your Apple device, there should be an area called "General". There you will find the item "Software update". Click or tap on it and see if an update is available. Alternatively, look under "About" (on the Mac also in the menu under "About this Mac") to see which operating system is currently installed. If it is one of the above, then everything is fine.
Apple lists the vulnerabilities closed in May 2023
An overview of current and past security updates for Apple systems can be found in the support document HT201222. Some time after the respective update, the associated content lists are also linked there. I mainly looked at the documents for iOS 16.5 / iPadOS 16.5 (here) and for macOS 13.4 (here) watched. Both individually and collectively, there are a number of closed security gaps. These are broken down into these areas:
- Accessibility (multiple)
- AppleMobileFileIntegrity
- Associated domains
- Contacts
- Location services
- CoreServices
- CUPS
- dcerpc
- Desktop Services
- ImageIO
- IOSurface
- IOSurfaceAccelerator
- kernel (multiple)
- LaunchServices
- Metal
- Mobile
- package kit
- PDFKit
- Photos
- Sandbox
- Screensavers
- Shell
- shortcuts
- Crab
- SQLite
- StorageKit
- settings or system settings
- Telephone function
- TV app
- weather app
- WebKit (multiple)
- WiFi
- and a few more
While some apps, settings, and system areas are familiar, other items on the lists are things that are not so familiar to the layperson. All the better that people look around for corresponding loopholes and report them to Apple. These people are named in the documents shown and in other documents – in addition to individuals and partly anonymous reports, there are also people from well-known companies and security departments. Team members from MacPaw, Google Project Zero and FFRI Security are named.
Related Articles
After graduating from high school, Johannes completed an apprenticeship as a business assistant specializing in foreign languages. But then he decided to research and write, which resulted in his independence. For several years he has been working for Sir Apfelot, among others. His articles include product introductions, news, manuals, video games, consoles, and more. He follows Apple keynotes live via stream.